Configure your hopsworks cluster to use OAuth2 for user management.#
If you want to use your organization's OAuth 2.0 identity provider to manage users in your hopsworks cluster this document will guide you through the necessary steps to register your identity provider in Hopsworks.ai.
Before registering your identity provider in Hopsworks you need to create a client application in your identity provider and acquire a client id and a client secret. Examples on how to create a client using Okta and Azure Active Directory identity providers can be found here and here respectively.
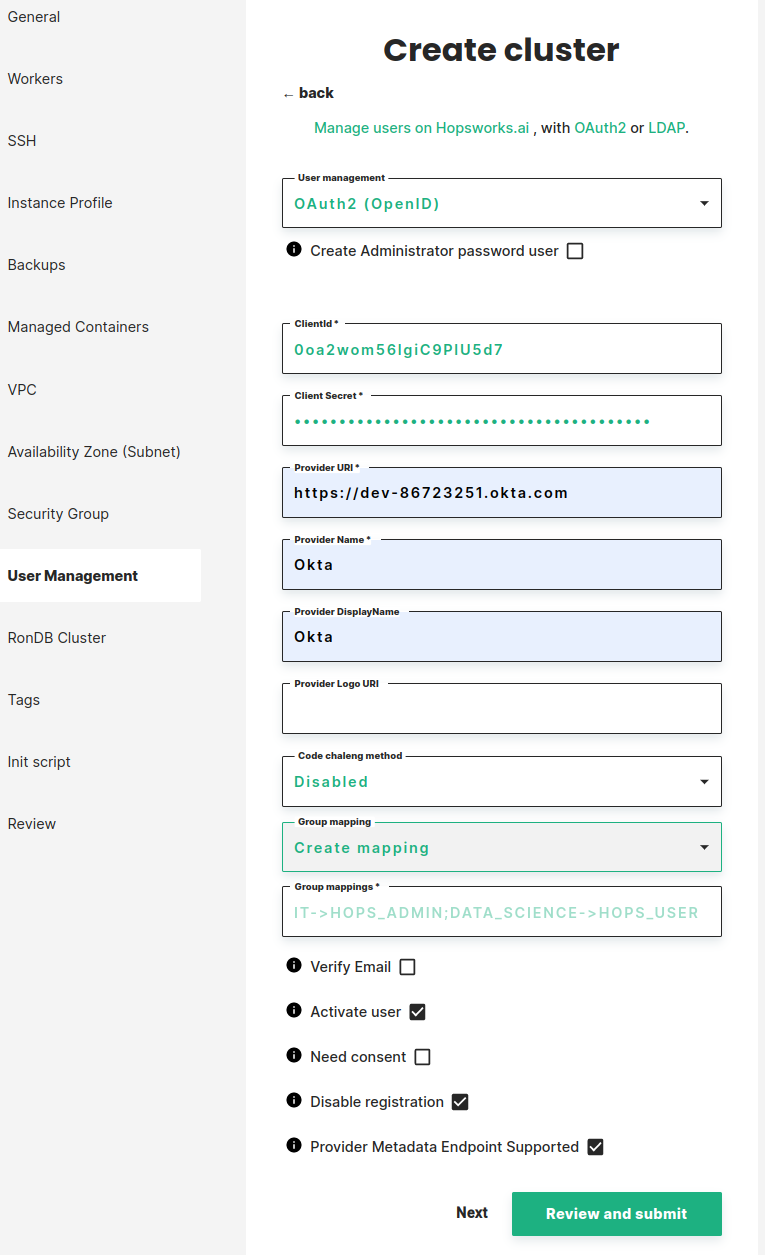
In the User management step of cluster creation (AWS, Azure) you can choose which user management system to use. Select OAuth2 (OpenId) from the dropdown and configure your identity provider.
Register your identity provider by setting the following fields:
- Create Administrator password user: if checked an administrator that can log in to the hopsworks cluster, with email and password, will be created for the user creating the cluster. If Not checked a group mapping that maps at least one group in the identity provider to HOPS_ADMIN is required.
- ClientId: the client id generated when registering hopsworks in your identity provider.
- Client Secret: the client secret generated when registering hopsworks in your identity provider.
- Provider URI: is the base uri of the identity provider (URI should contain scheme http:// or https://).
- Provider Name: a unique name to identify the identity provider in your hopsworks cluster. This name will be used in the login page as an alternative login method if Provider DisplayName is not set.
Optionally you can also set:
- Provider DisplayName: the name to display for the alternative login method (if not set Provider Name will be used)
- Provider Logo URI: a logo URL to an image. The logo will be shown on the login page with the provider name.
- Code Challenge Method: if your identity provider requires a code challenge for authorization request check the code challenge check box. This will allow you to choose a code challenge method that can be either plain or S256.
- Group Mapping: will allow you to map groups in your identity provider to groups in hopsworks.
You can choose to map all users to HOPS_USER or HOPS_ADMIN. Alternatively you can add mappings as in the example below.
This will map users in the IT group in your identity provider to HOPS_ADMIN and users in the DATA_SCIENCE group to HOPS_USER.
IT->HOPS_ADMIN;DATA_SCIENCE->HOPS_USER - Verify Email: if checked only users with verified email address (in the identity provider) can log in to Hopsworks.
- Activate user: if not checked an administrator in hopsworks needs to activate users before they can login.
- Need consent: if checked, users will be asked for consent when logging in for the first time.
- Disable registration: if unchecked users will have the possibility to create accounts in the hopsworks cluster using user name and password instead of OAuth.
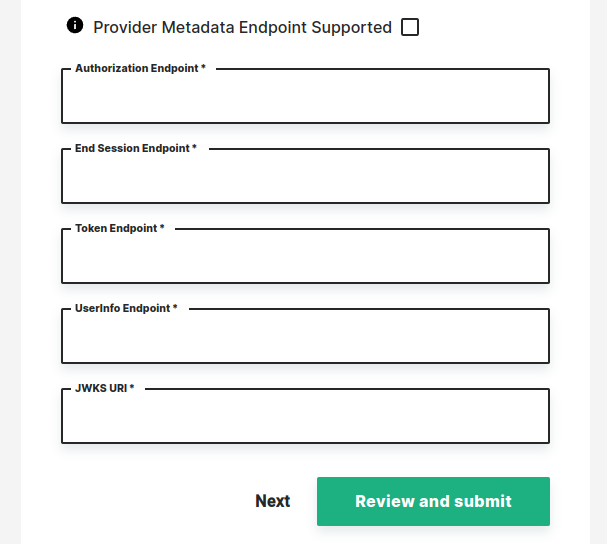
- Provider Metadata Endpoint Supported: if your provider defines a discovery mechanism, called OpenID Connect Discovery,
where it publishes its metadata at a well-known URL, typically
you can check this and the metadata will be discovered by hopsworks. If your provider does not publish its metadata you need to supply these values manually.
https://server.com/.well-known/openid-configuration
- Authorization Endpoint: the authorization endpoint of your identity provider, typically
https://server.com/oauth2/authorize - End Session Endpoint: the logout endpoint of your identity provider, typically
https://server.com/oauth2/logout - Token Endpoint: the token endpoint of your identity provider, typically
https://server.com/oauth2/token - UserInfo Endpoint: the user info endpoint of your identity provider, typically
https://server.com/oauth2/userinfo - JWKS URI: the JSON Web Key Set endpoint of your identity provider, typically
https://server.com/oauth2/keys
After configuring OAuth2 you can click on Next to configure the rest of your cluster.
You can also configure OAuth2 once you have created a Hopsworks cluster. For instructions on how to configure OAUth2 on Hopsworks see Authentication Methods.