Configure your Hopsworks cluster to use LDAP for user management.#
If you want to use your organization's LDAP as an identity provider to manage users in your Hopsworks cluster this document will guide you through the necessary steps to configure managed.hopsworks.ai to use LDAP.
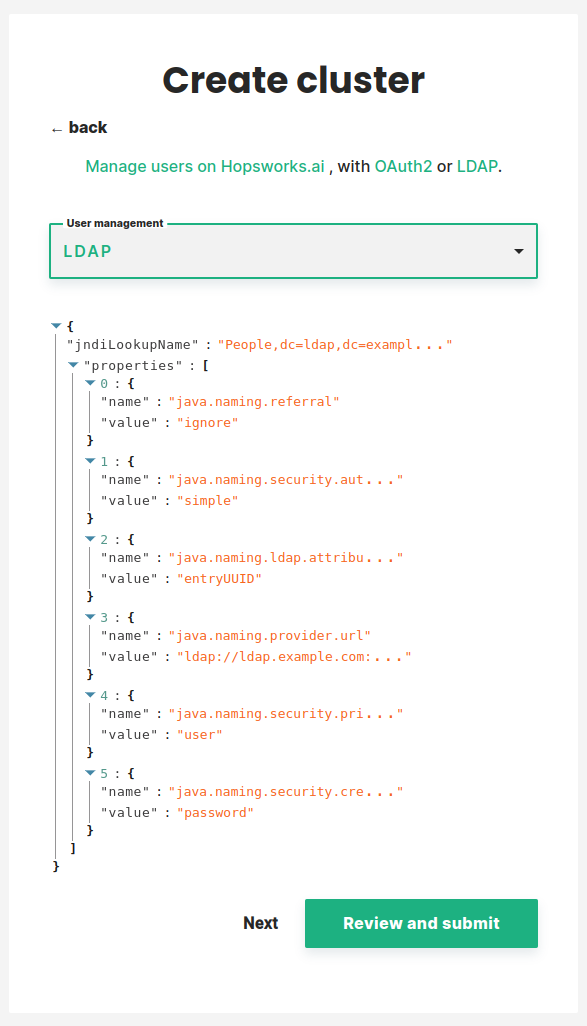
The LDAP attributes below are used to configure JNDI resources in the Hopsworks server. The JNDI resource will communicate with your LDAP server to perform the authentication.
- jndilookupname: should contain the LDAP domain.
- java.naming.provider.url: url of your LDAP server with port.
- java.naming.ldap.attributes.binary: is the binary unique identifier that will be used in subsequent logins to identify the user.
- java.naming.security.authentication: how to authenticate to the LDAP server.
- java.naming.security.principal: contains the username of the user that will be used to query LDAP.
- java.naming.security.credentials: contains the password of the user that will be used to query LDAP.
- java.naming.referral: whether to follow or ignore an alternate location in which an LDAP Request may be processed.
After configuring LDAP and creating your cluster you can log into your Hopsworks cluster and edit the LDAP attributes to field names to match your server. By default all attributes to field names are set to the values in OpenLDAP. See Configure LDAP on how to edit the LDAP default configurations.
Note
A default admin user that can log in with username and password will be created for the user that is creating the cluster. This user can be removed after making sure users can log in using LDAP.